- Solutions
- Solutions primary
- BY TEAM
- BY INDUSTRY
- BY USE
- BY SIZE
- View all solutions
- Solutions secondary
- Solutions primary
- AI
- Features
- Features primary
- Most popular
- first column
- second column
- third column
- fourth column
- View all features
- Most popular
- Features secondary
- Choosing the right plan
- Features primary
- Integrations
- Integrations primary
- MOST POPULAR
- first column
- second column
- View all integrations
- NEW
- first column
- second column
- View all integrations
- MOST POPULAR
- Integrations secondary
- Integrations primary
- Pricing
- Resources
- Resources primary
- Most popular
- first column
- second column
- third column
- Most popular
- Resources secondary
- Latest Blogs
- Try CloudTalk
- Resources primary
- Partners
Get Easy Access to All Apps With Single Sign-On
Give users one account to use across all CloudTalk applications and integrations. Use Single Sign-On to optimize the login process, boost security, and create a more convenient user experience.
Simplify Your Sign-In Process
Improve Your Security
All CloudTalk’s products support SSO: Desktop, CTIs, iOS & Android apps, C2C and more!
Easily Manage Access
Let your IT team manage employee access directly through the SSO provider.
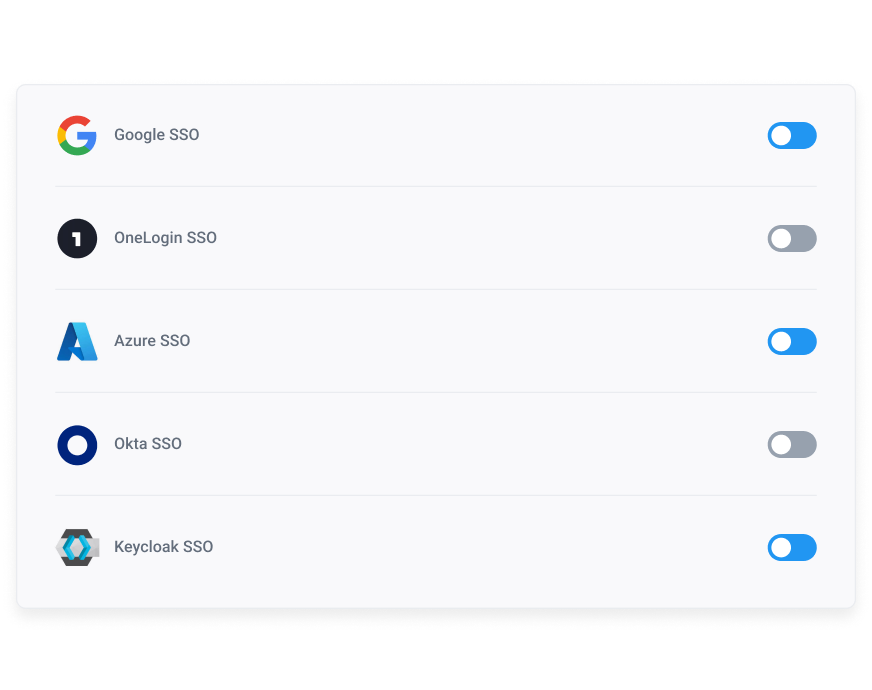
Choose Your Provider
CloudTalk is SSO-compatible with Salesforce, Azure, and 4 other industry leaders.
What is Single Sign-On (SSO)?
Single Sign-On (SSO) allows you to log in using just one set of credentials for multiple applications. With SSO, your team can access CloudTalk securely without the hassle of managing multiple passwords.
This improves security by reducing weak password use. The SSO also enhances productivity by streamlining the login process. By integrating it with your existing identity provider, you can ensure that only authorized users gain access to CloudTalk, giving you better control and peace of mind.
How Does SSO Work?
Single Sign-On (SSO) works by allowing users to authenticate once through a trusted identity provider, granting them access to CloudTalk and other connected applications without needing to log in again.
When a user attempts to access CloudTalk, SSO verifies their credentials with the identity provider, which then confirms their identity and grants access. This process not only strengthens security but also reduces login friction.
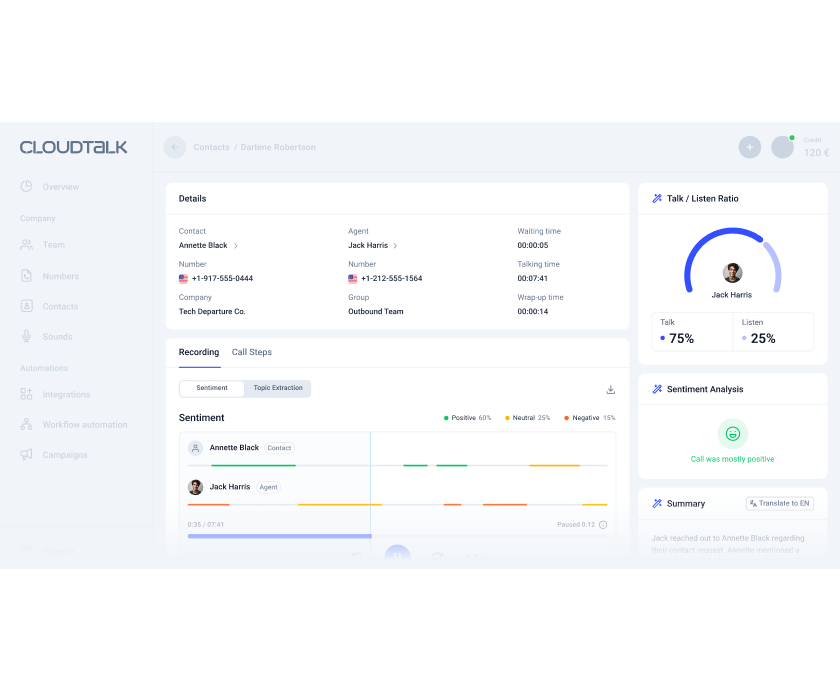
4 Key Benefits of Single Sign-On
Improve User Experience
Boost your productivity and keep things running smoothly by using one set of credentials to access multiple applications, including CloudTalk. Focus on your tasks without interruptions, enjoying a seamless experience that makes your day easier.
Increase Your Data Security
Get rid of weak or reused passwords. Implement stronger security measures like multi-factor authentication (MFA) and ensure only the right people have SSO access. Be less vulnerable to credential-related threats and keep data safe.
Simplify IT Management
Save time on employee onboarding or offboarding. Easily control and update permissions across all applications from a single platform. See fewer helpdesk requests for password resets. Free up resources for more important tasks please your customers.
Easily Monitor Compliance
Get a centralized way of following user activity and monitor obedience with data protection regulations. Gain a clear audit trail of SSO login activities, helping you meet compliance requirements with ease. Enforce security policies across all apps.
Decrease logging time, increase security.
How to Use Single Sign-On in CloudTalk?
01
Open your CloudTalk account and log in.
02
From the Dashboard, navigate to the “Account Settings” section.
03
In Account Settings, select the “Security” tab.
04
Click on the option to enable SSO for your account.
05
Enter the necessary details from your identity provider (e.g., metadata, entity ID, etc.).
06
Once everything is filled out, save the SSO configuration to activate it for your account.
07
Log out and log back in using SSO to verify the setup is working properly.
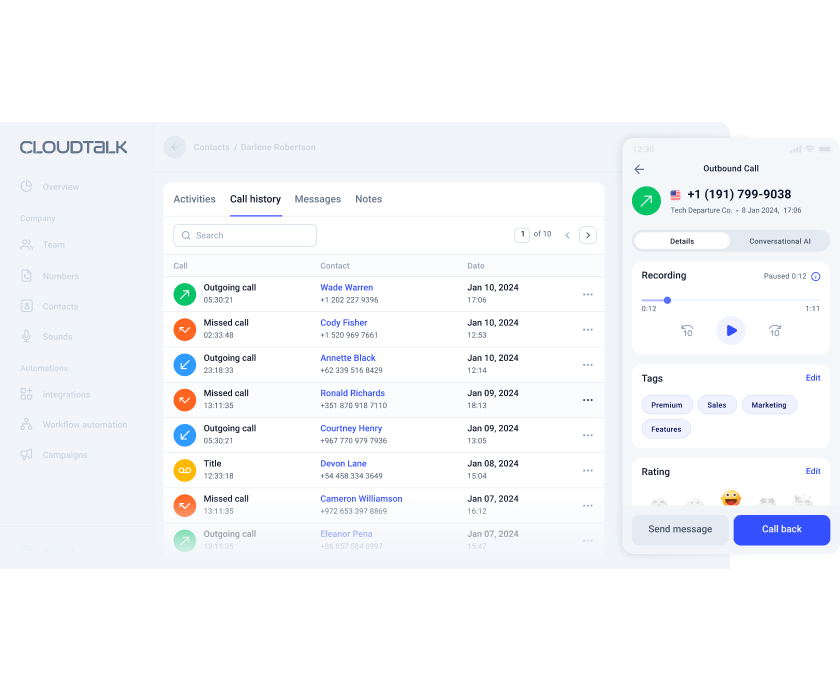
Other features you might like
Turn your CloudTalk into a much larger and powerful tool
Expand your business toolstack with a business calling software that can be easily integrated into your existing CRMs, ecommerce or helpdesk tools, like Salesforce, Freshdesk, Help Scout, and dozens more.
Have questions?
What is an SSO Token?
An SSO token is a digital credential generated after a user successfully authenticates through Single Sign-On. It contains user identity information and allows access to multiple applications without needing to log in again. The token is securely passed between systems to verify the user’s identity.
How do SSO Authentication Tokens Work?
SSO authentication tokens work by containing encrypted information about a user’s identity, which is issued by an identity provider after a successful login. When accessing other connected applications, the token is validated by these applications to grant the user access without requiring additional logins. This process enables seamless transitions between systems.
Is SSO Secure?
Yes, SSO is secure when implemented correctly. It reduces the number of login credentials users need to manage, thereby lowering the risk of weak or reused passwords. SSO supports security features like multi-factor authentication (MFA), centralized control, and monitoring, further strengthening security by minimizing potential vulnerabilities across systems.
Are There Different Types of SSO?
Yes, there are different types of SSO. Some common types include SAML (Security Assertion Markup Language), OAuth, and OpenID Connect. These protocols differ in how they handle secure authentication, but they all enable users to log in once and access multiple systems or applications.
What is an Example of an SSO?
An example of SSO is logging into Google and then accessing Gmail, Google Drive, and YouTube without needing to log in again for each service. The single login through Google’s identity provider allows seamless access to all connected applications.
What Happens if a Single Sign-On is Enabled?
When Single Sign-On is enabled, users only need to log in once using their credentials from an identity provider. After that, they can access all authorized applications without needing to log in again. This simplifies the user experience, strengthens security, and centralizes access management for the organization.
Ready to get started?
Schedule a demo with one of our specialists and gain unparalleled control over your customer’s experience.